A cookie is a text file carrying some information that a website places on a user’s computer. It allows the website to identify the user and improve their future web browsing experience.
A web server generates cookies, also known as browser cookies, web cookies, HTTP cookies or internet cookies, and sends them to the user’s web browser. They store limited information from a web browser session on a given website; the website can then retrieve them when the user opens it in the future.
Cookies first appeared in 1994 as part of the (now-defunct) Netscape Navigator web browser. They helped the browser understand if a user had already visited a given website. Netscape developer Lou Montulli invented the initial cookie implementation. He was granted U.S. Patent No. 5,774,670A, with the description, “Persistent client state in a hypertext transfer protocol-based client-server system.”
Purpose of cookies
The most common use cases for cookies are user tracking, user experience (UX) personalization and session management.
Consider user tracking and UX personalization. A website that collects and then stores cookies can remember some useful information about a user. More importantly, it can retrieve this information when the user returns to the site to identify the user and present them with more relevant content and experiences.
For example, an e-commerce website might use a persistent cookie to remember details about a book purchased by User A in January 2025. Then, when User A returns to the site in May 2025, the browser will retrieve and read the cookie and the site will present User A with a list of other books on the same topic or by the same author. These lists might enable User A to save time as they shop. User A might also see ads for similar books or other related products.
Similarly, the web browser will store User A’s username for the website within a session cookie. When User A loads that website the next time, the web browser sends the information to the web server, which will then prompt User A to log in with that username. Once User A logs in, the site will load their account content and might even display a personalized message on the homepage, such as “Welcome, [User A].”
How cookies work
When a user opens a website, such as https://www.techtarget.com, the web server generates cookies. These information files contain information about the user and are stored in a designated file on the user’s device for a certain time, such as the length of the user’s session on that website or for a few months.
When the user opens a session with the website in the future — in general, makes some future request of the same web server — the cookies are attached to the request. The information in the cookie file enables the website to “recognize” the user and, accordingly, personalize and enhance their browsing experience.
Here is a step-by-step explanation of how website cookies work:
- The user visits a website.
- Information about the user, such as their username, pages visited, content viewed, etc., is stored in a small information file.
- The file is linked to the user and the user’s computer, meaning it is assigned a unique ID;
- The file is then stored on the website’s server and remains there even if the user leaves the site.
- When the user returns to the site later, the user’s browser gives the cookie to the website.
- The website reads the cookie, identifies the user and device from the unique ID, and assembles the user’s activity data.
- Finally, the website presents relevant and personalized data and content to the user.
Types of cookies
There are multiple types of cookies that run in modern web browsers with specific use cases to enable certain capabilities. These include the following:
- HTTP cookies. This is the overall category of computer cookies used with modern web browsers. HTTP cookies are used to capture user data during a website session, track users and user activity, and deliver personalized content and customized browsing experiences. Some cybercriminals also use HTTP cookies to spy on users and steal user information. All the cookies in this list — except for flash cookies — are forms of HTTP cookies.
- Session cookies. A session cookie is only persistent while the user is navigating or visiting a given website. Its purpose is to track a user’s single website session, so it is deleted when the session ends. A session will end when the user either exits the website completely or logs out of their account on that website. Session cookies are stored in the computer’s RAM instead of its HD, and have no expiration date. These features tell the browser the session cookie should be deleted when the session ends.
- Persistent cookies. Also known as permanent cookies, persistent cookies are not deleted at the end of the user’s website session. They endure for a configurable time or until a certain date set by the web server. The expiration date of the persistent cookie tells the browser when to delete it. Persistent cookies are mainly used to authenticate users (confirm that they are who they say they are), to track a user’s visits to the same site over time, and to personalize each of those visits.
- Authentication cookies. These persistent cookies are generated when a user logs in to their account on a specific website. The cookies ensure that sensitive user information (especially passwords) is delivered to the correct sessions to authenticate the user and prevent unauthorized users from logging in to the account.
- Tracking cookies. These cookies record user activity over multiple visits to a website on behalf of a tracking service. Based on this information, the tracking service builds a user profile to understand the user and improve their browsing experiences over time.
- Zombie cookies. This refers to a type of persistent cookie that persists, even after the user attempts to delete it. While many zombie cookies are harmless and simply annoying to the user, some help hackers infect user systems with viruses or malware.
- Flash cookies. These are not browser or HTTP cookies but, rather, a specific type of cookie that works with Adobe Flash. With the decline in the use of Flash and the discontinuation of Flash Player support by Adobe in January 2021, these cookies are no longer widely used.
- Secure cookies. These are first- and third-party cookies that can only be sent over encrypted HTTPS connections.
First-party cookies vs. third-party cookies
Cookies can be accessed by the site a user is on (first-party cookies) or by a third-party site (third-party cookies).
First-party cookies are also known as SameSite cookies because the cookie and information it contains are restricted to the same site on which it was set. These cookies are created by the website the user is currently visiting. Thus, when User A opens https://www.techtarget.com on their browser, the origin server for the TechTarget website creates a first-party session cookie to remember User A.
First-party cookies are usually used to do the following:
- Remember user settings like language preferences, login details or pages visited.
- Improve site functionality for that user.
- Personalize user experiences during subsequent visits to that site.
These cookies are not very intrusive and are generally safe because they are only used on the website the user is currently visiting. However, they can pose a security risk if the website is not reputable.
Third-party cookies are not restricted to the initial site where the cookie was created. They enable entities other than the original site. So, when User A visits a site http://www.site.com, a cookie from both site.com and example.ad-company.com might get stored in their browser. The former is a first-party cookie; the latter is a third-party cookie. The third-party cookie enables, for example, an ad company to track users and then target them for personalized ads.
Due to the security and privacy concerns posed by third-party cookies, many browsers, including Google Chrome and Mozilla Firefox, let users manage and control them through their browser settings. Similarly, many devices, including Android and Apple devices, also allow users to disable third-party (and first-party) cookies.
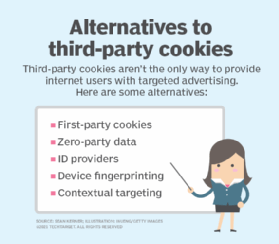
Third-party cookies are not the only way to provide targeted advertising and marketing to internet users; there are viable alternatives.
Are cookies safe?
Cookies have been part of daily internet operations for decades and are generally safe. However, third-party cookies are sometimes seen as intrusive and can put a user’s privacy and information at risk of leaks and breaches.
Third-party cookies enable entities such as advertisers to track user activity to provide targeted ads to the user. However, they often collect this information in a way that users are not aware of, thus deliberately and clandestinely infringing on the user’s privacy. This is a huge concern for many who don’t want to be tracked or have their browsing habits shared.
There is also the potential for threat actors to hijack third-party cookies. This would give them access to user information and enable them to launch other types of attacks, such as session hijacking, cross-site scripting (XSS) and cross-site request forgery.
Unsecured cookies can also be a security risk for users and website operators. Unlike secure cookies that only send information using secure HTTPS connections to the origin website or to a third party, unsecure cookies are transmitted unencrypted over less-secure HTTP connections. The risk of information leaks or privacy breaches is minimal if the information is something simple, such as whether the user has visited the site before. However, some sites use cookies to store sensitive user information — including personally identifiable information (PII) such as authentication credentials and payment card details. If such data is sent unencrypted, a criminal can intercept it.
The SameSite attribute can mitigate these risks. By using this attribute in the HTTP cookies, web servers can also specify whether or when third-party cookies can be sent. This attribute controls when a browser sends a cookie with a cross-site request (a request where the site sending the cookie request is different from the site the user is currently visiting). In doing so, it prevents cross-site data leaks and cross-site forgery attacks and preserves user privacy.
Many privacy regulations also incorporate cookie-related considerations to reduce the privacy risks of HTTP cookies. Cookies that can identify users are now subject to strict rules under the General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) regulations.
How to manage cookies on different web browsers
Every major web browser has a set of controls to help users configure what types of cookies to accept and delete. Here’s how to block third-party cookies in Apple Safari, Google Chrome, Microsoft Edge and Mozilla Firefox.
To block third-party cookies in Apple Safari
Here is how to block third-party cookies in Safari:
- Open Safari.
- Click Safari > Preferences in the upper left-hand corner of the screen.
- Click on the Privacy tab.
- Next to Cookies and website data, the Block all cookies option appears. Check this option to disable all cookies.
- Restart Safari.
Unchecking the Block all cookies option will enable all cookies. Under this option, there is a box marked Manage Website Data; this is where all the collected cookies can be viewed and managed.
In Safari, all first-party cookies are set to expire after seven days by default.
To block third-party cookies in Google Chrome
In Chrome, users can block third-party cookies by doing the following:
- Open Chrome.
- In the top-right corner, click Settings.
- Click Privacy and security.
- Click Third-party cookies,
- Three options are available:
- Allow third-party cookies.
- Block third-party cookies in Incognito mode.
- Block third-party cookies.
- Select option #3 to block all third-party cookies.
This procedure will disable third-party cookies in Chrome on a Windows PC, MacBook and Android mobile devices.
To block third-party cookies in Microsoft Edge
Follow these steps to block third-party cookies in the Edge browser:
- Open Microsoft Edge.
- In the top-right corner, select Settings.
- SelectCookies and site permissions.
- Under Cookies, select Cookies and site data.
- Enable Block third-party cookies.
Disabling Allow sites to save and read cookie data (under Cookies and site data) will block all cookies, including first-party cookies.
Edge also allows users to block cookies from specific sites:
- Navigate to Cookies and site data.
- Navigate to the Block section.
- Select Add to block cookies for a site by entering its URL.
To block third-party cookies in Mozilla Firefox
In Firefox, users can block third-party cookies in this way:
- Open Firefox.
- In the top-right corner, click Settings.
- Click Privacy & Security.
- Select one of the options to manage cookies and maintain privacy: Standard, Strict or Custom.
- If the Standard or Strict options are selected, Firefox automatically blocks all cross-site (third-party) cookies. With the Custom option, the user can choose which trackers and scripts to block, including cookies and other types of tracking content.
Besides using these settings, users can also choose to delete cookies when Firefox is closed. This can be done by checking the box for Delete cookies and site data when Firefox is closed under Cookies and Site Data.
To clear all cookies saved to the computer:
- Navigate to Cookies and Site Data.
- Click on Clear Data.
- Check the box for Cookies and site data.
First-party cookies play a significant role in tracking user engagement, while third-party cookies are integral to various marketing and sales strategies. It’s interesting to note that, despite their different applications, the two types of cookies also have several similarities worth considering. Explore how first-party versus third-party cookies are similar and different. Also, learn what a supercookie is and read about the danger of the cyberattack known as cookie poisoning.


