Mishaal Rahman / Android Authority
TL;DR
- Google is adding an optional Android 16 feature to disable USB data access when the phone is locked for enhanced security.
- This protects against attackers from using USB devices to extract data or bypass the lock screen on lost or confiscated phones.
- Tied to the new Advanced Protection Mode, it blocks new USB peripherals until the device is unlocked and the USB is reinserted.
If you’re serious about security, then you probably already avoid inserting random USB sticks into your personal devices. It’s good practice to be cautious of unknown USB devices, especially since you don’t know what kinds of payloads they might contain. But if your Android device is lost or confiscated, then you can’t stop someone else from inserting a USB device. To protect against this, Google is working on a new, optional feature in Android 16 that disables USB access when your phone is locked.
You’re reading an Authority Insights story. Discover Authority Insights for more exclusive reports, app teardowns, leaks, and in-depth tech coverage you won’t find anywhere else.
It might sound like paranoia, but there are valid reasons why one might want to block USB devices when your Android phone is locked. If you’re a journalist or activist who is at risk of being targeted by hackers, you’ll want to take every precaution you can to prevent your phone’s contents from being extracted. USB peripherals like keyboards can be used to brute force the keyguard, while other devices can inject payloads that exploit vulnerabilities to unlock the device. This isn’t hypothetical — Amnesty International’s Security Lab recently documented a zero-day USB driver exploit that was used to break into the phone of a student activist in Serbia.
The best way to stop these kinds of attacks is to disable USB data signaling, preventing USB devices from sending data to locked Android devices. This can be achieved in two ways: through hardware or software controls. Disabling USB data signaling at the hardware level cuts off the USB data lines entirely. Charging will still work, of course, but all peripherals—including keyboards, mice, flash drives, and even external displays—will not.
According to the GrapheneOS team, implementing this hardware-level feature requires changes to USB drivers. In contrast, the software-level approach involves disabling high-level USB support, essentially blocking connections from new peripherals and gadgets when the device is locked. While either method would have thwarted the exploit documented by Amnesty International, the hardware-based approach offers slightly stronger security.
With the release of Android 12 in 2021, Google introduced an API for disabling USB data signaling at a software level. This API was made available to device admin apps, i.e. apps that manage enterprise devices. It wasn’t used in any other context until the release of Android 15 last year, which enhanced the operating system’s lockdown mode to also disable USB data access. Now in Android 16, Google is looking to use this API to disable USB data access when your Android device is locked, but only if you enable Advanced Protection Mode.
Advanced Protection Mode is a new feature in Android 16 that enables extra security features for people who opt in. It builds upon Google’s Advanced Protection Program, a security program that provides extra protection against hackers getting into your Google account. When Advanced Protection Mode is enabled in Android 16, apps can’t be granted the sideloading permission, 2G access can’t be enabled, MTE is enabled for compatible apps, and WEP connections are blocked. In addition, apps can query the Advanced Protection Mode API to know when a user has opted in and then enable their own set of security features. As revealed in an APK teardown, apps like Phone by Google and Messages are poised to support Advanced Protection Mode.
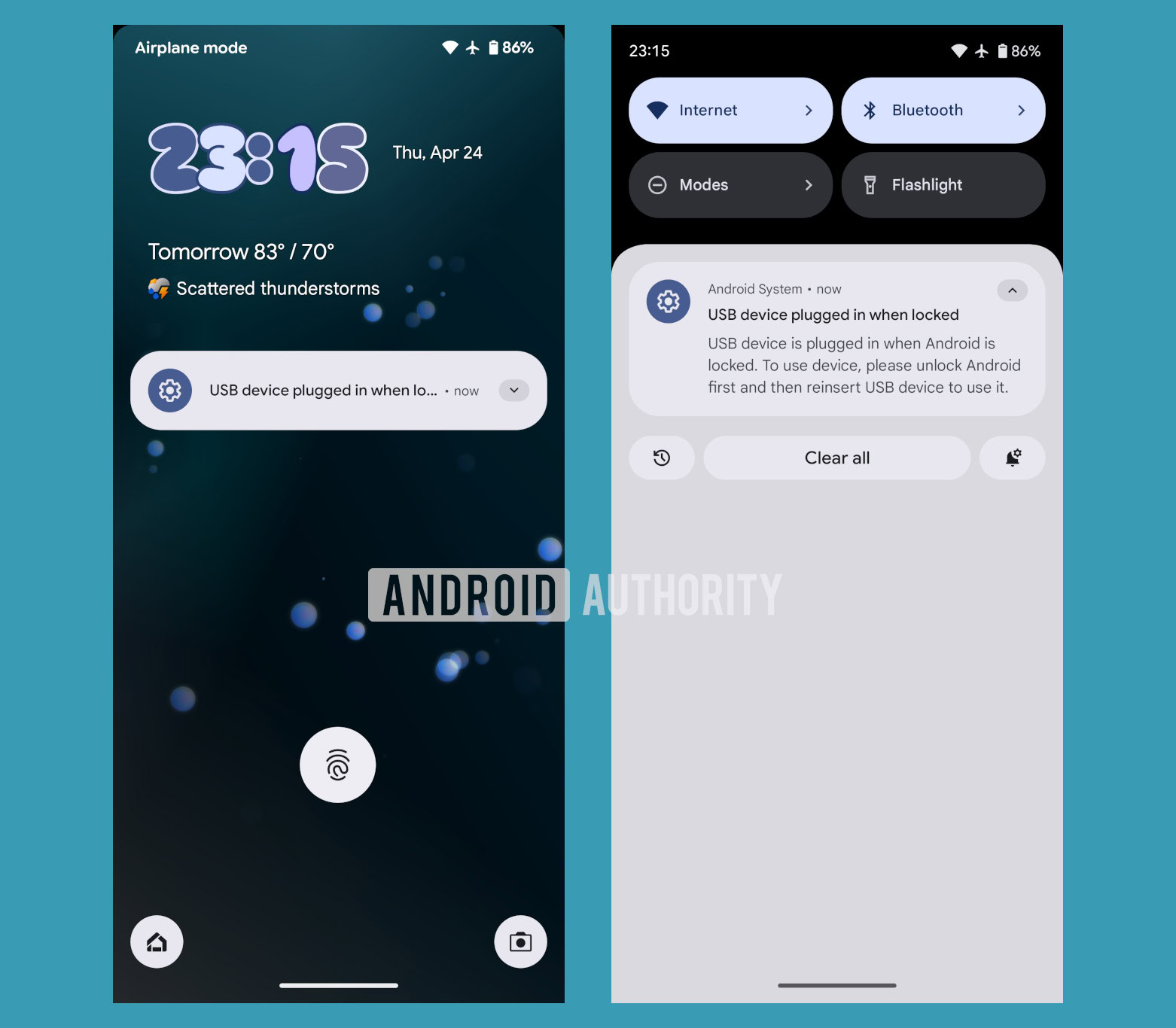
While digging through the recent Android 16 betas, I found strings that suggest enabling Advanced Protection Mode will also disable USB data signaling when Android is locked. The titles of each string have “_apm_” in them, which stands for Advanced Protection Mode internally. They also explicitly mention how new USB devices can’t be used when Android is locked. When a new USB device is plugged in, a notification will appear that warns the user of “suspicious USB activity.” To use the device, you have to “unlock Android first and then reinsert [the] USB device to use it.”
Code
USB device is plugged in when Android is locked.
To use device, please unlock Android first and then reinsert USB device to use it.
USB device plugged in when locked
USB data signal has been disabled.
Suspicious USB activity Google has yet to roll out a user-facing way to enable Advanced Protection Mode, but I was able to manually enable it in Android 16 Beta 4. After enabling it, I was able to get the new USB data protection working, as shown in the video embedded below.
As you can see in the video, Android rejects both the USB stick and the keyboard I inserted into my Pixel device when it was locked. Only after unlocking and reinserting both items was I able to use them. After inserting them and then locking the device, they weren’t disconnected—suggesting that Android won’t forcibly disconnect USB devices with an active data connection.
Mishaal Rahman / Android Authority
This is a simple security change that should prevent cases like the one described in the Amnesty International report from happening again. Hopefully Google rolls out a way to toggle Android 16’s new Advanced Protection Mode soon, because it’ll serve as an easy one-click toggle to enable a lot of features that security-conscious users will enjoy.


